Table of Contents
- Understanding DDoS Attacks
- IP Grabbers and Their Usage
- Grabify Tools and Their Impact
- Efficient Booter Tools
- IP Spoofing and Layer 4 Attacks
Understanding DDoS Attacks
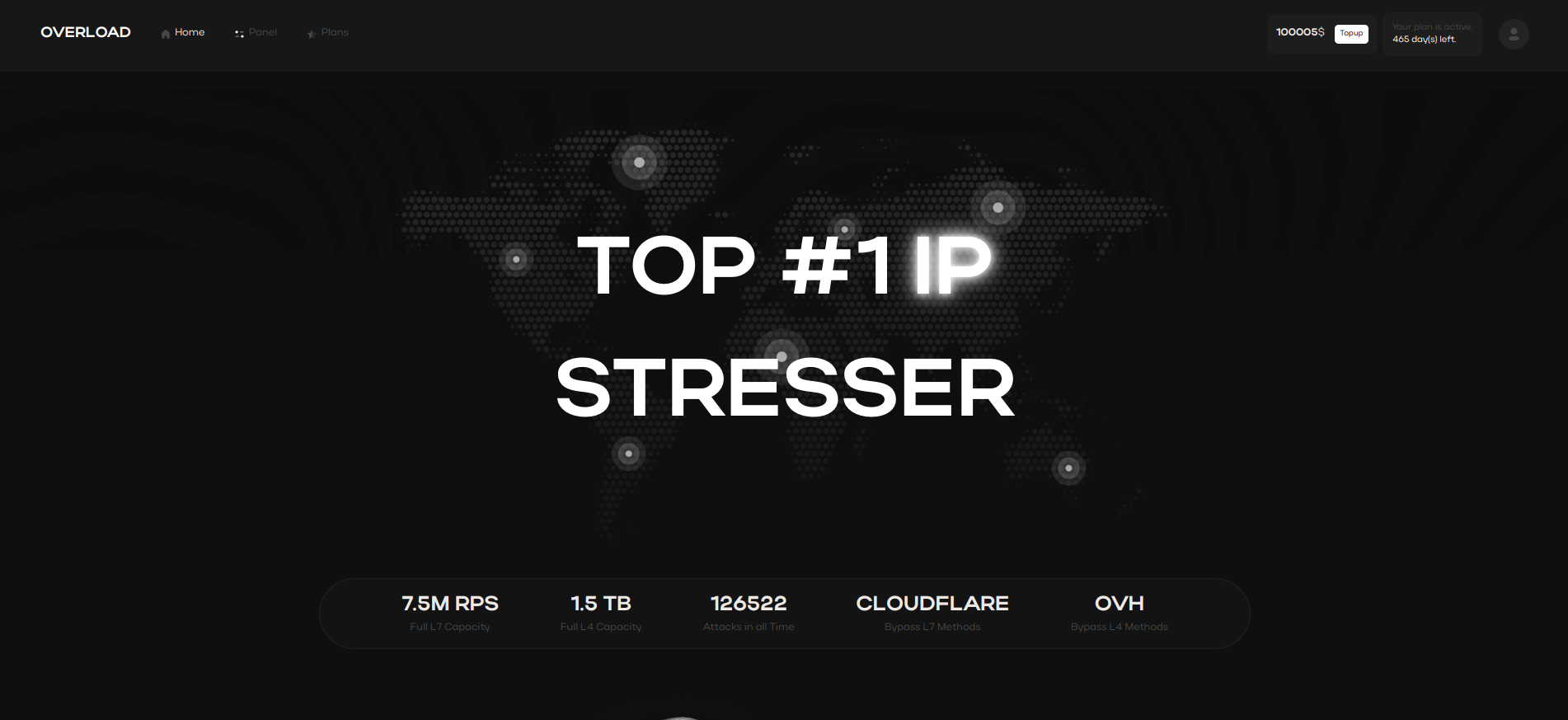
Distributed Denial of Service (DDoS) attacks flood networks with excessive requests, crippling services.
By analyzing their patterns, organizations can deploy proactive defenses and safeguard their critical infrastructure.
IP Grabbers and Their Usage
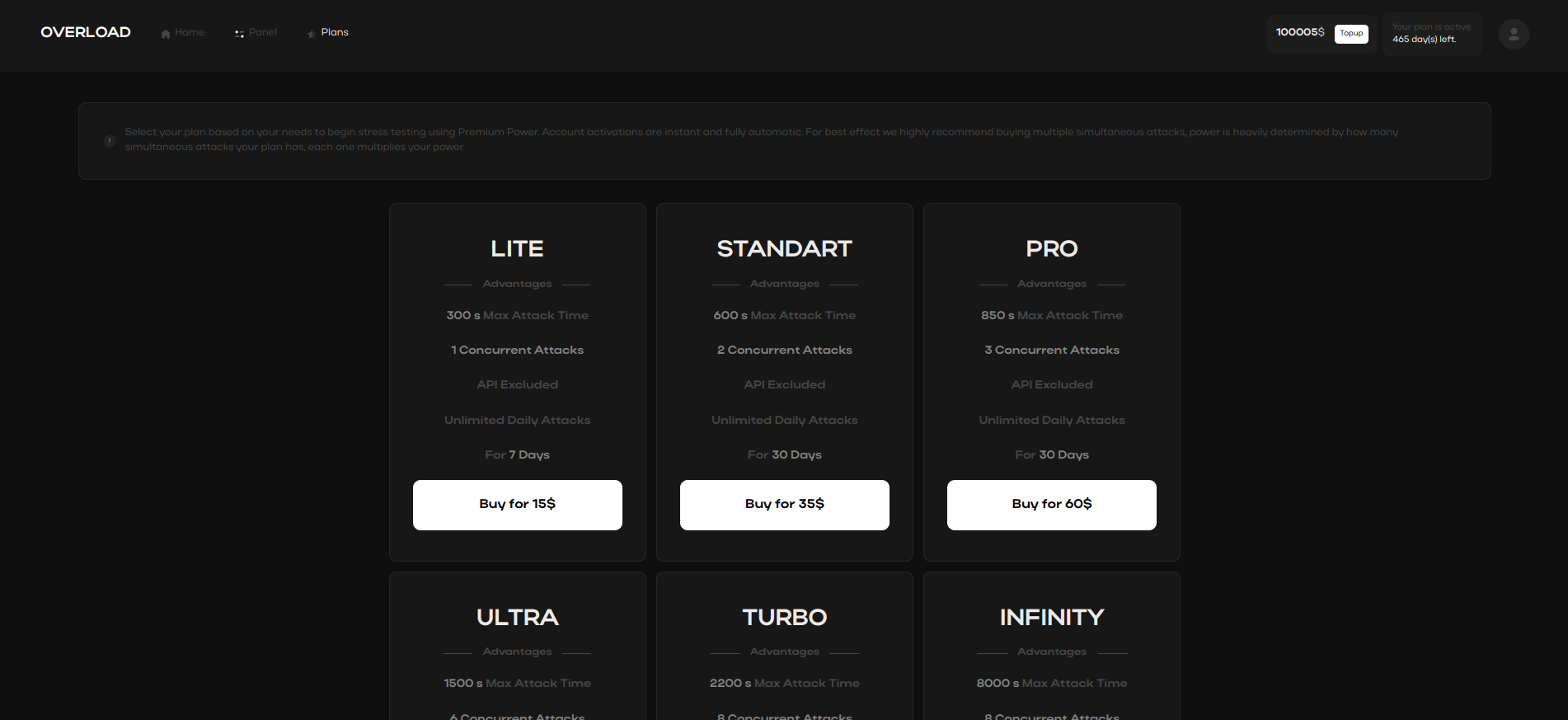
By analyzing traffic patterns, IP grabbers highlight vulnerabilities
in infrastructure, enabling proactive defenses against cyber threats.
Grabify Tools and Their Impact

Grabify tools are designed to monitor and analyze traffic patterns.
They support cybersecurity measures by identifying potential threats and aiding in incident prevention.
Efficient Booter Tools

Efficient booter tools streamline load testing,
providing actionable insights to improve server performance and handle peak loads.
IP Spoofing and Layer 4 Attacks
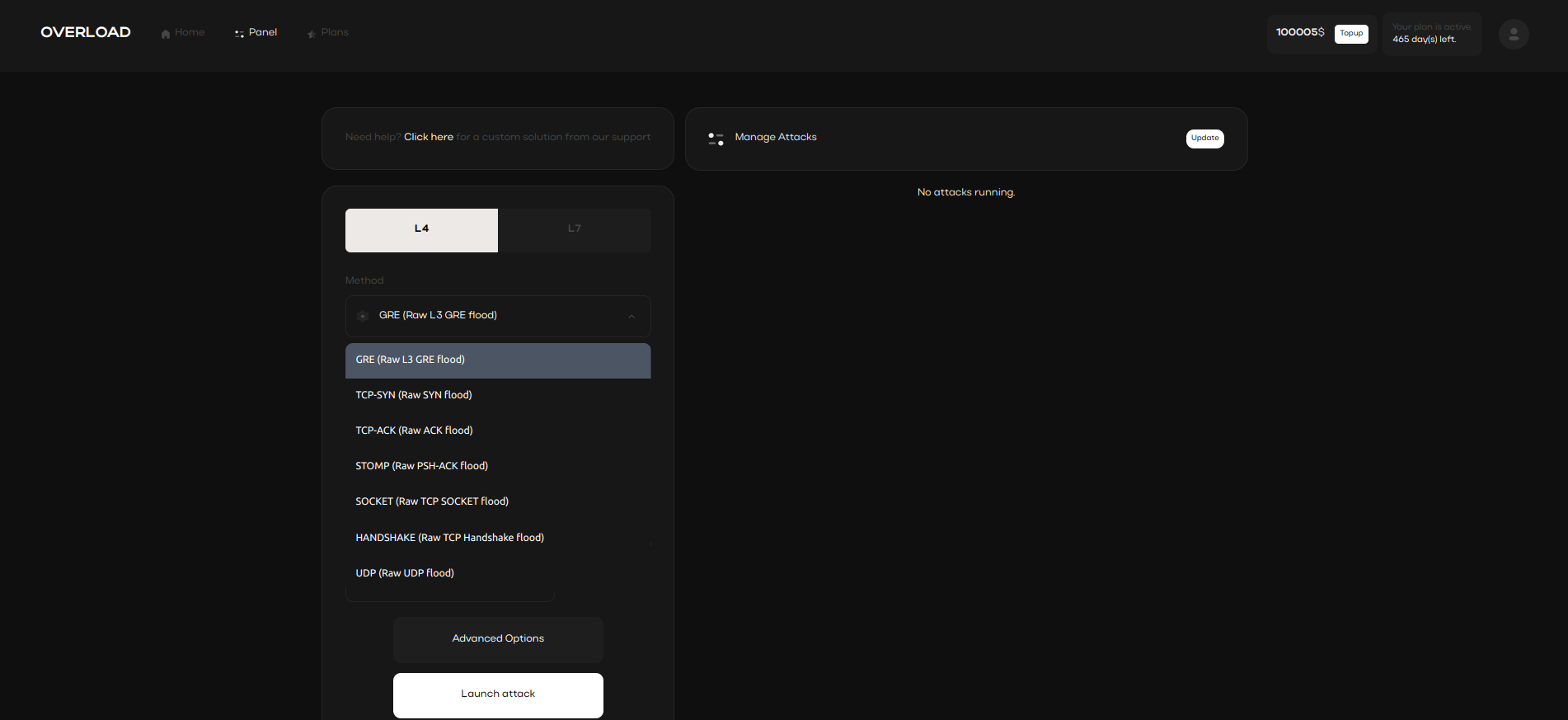
IP spoofing techniques in network-based intrusions can
conceal attack origins, making it harder to trace attackers.
Spoofing provides an added layer of anonymity, which is critical in maintaining stealth during network tests.
hardstresser
stresser io
v booter
ddos programs
ddos attack service provider
storm stresser
ddos programs
bullstresser
ddos website online
ddos attack tool download
meris ddos botnet
https www stressthem to login
vps for ddos
stresser ai
botnet ddos attack tutorial
c2 ddos
ddos booter
ddos attack
ip booter github
ddosim download
ddos test
5 min booter

